“Simjacker has been even further exploited to execute many other forms of attacks against people today and mobile operators such as fraud, scam calls, facts leakage, denial of provider and espionage. AdaptiveMobile Security Risk Intelligence analysts noticed the hackers vary their assaults, testing quite a few of these more exploits. In theory, all makes and models of mobile cell phone are open up to attack as the vulnerability is connected to a technological innovation embedded on SIM playing cards. The Simjacker vulnerability could lengthen to around 1 billion cell phone users globally, likely impacting nations around the world in the Americas, West Africa, Europe, Middle East and indeed any region of the planet wherever this SIM card know-how is in use.”-AdaptiveMobileSecurity
Some figures were tracked hundreds of moments in excess of the study course of a 7 days
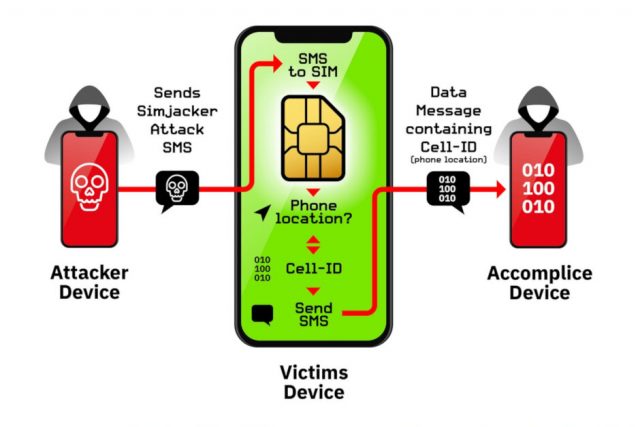
The report indicated that people are being tracked each day by Simjacker with some certain telephone numbers becoming tracked hundreds of times above a 7-working day period. The procedure of spying on a susceptible handset requires a inexpensive GSM modem to send out a message to a SIM card that consists of the S@T browser technological know-how. Using binary SMS, which is not the identical as typical textual content messages, phones can be instructed to accumulate the asked for facts and disseminate it to a negative actor. The exploration report notes that “Throughout the assault, the person is completely unaware that they obtained the attack, that information was retrieved, and that it was efficiently exfiltrated.”

Example of an early WAP browser
And Simjacker’s surveillance routines have now been broadened to “execute quite a few other sorts of assaults in opposition to persons and cell operators such as fraud, fraud calls, information leakage, denial of company and espionage.” The only optimistic point about this assault is that it depends on older know-how that in concept need to be phased out. But until finally the S@T technological innovation is entirely removed from all SIM playing cards, Simjacker stays a threat. And as AdaptiveMobile Security’s main technology officer Cathal Mc Daid stated, “Now that this vulnerability has been exposed, we completely expect the exploit authors and other destructive actors will check out to evolve these assaults into other regions.”
The GSM Affiliation trade overall body states that it has been built informed of Simjacker and states that it has worked with the researchers and the mobile industry to discover which SIM playing cards are impacted, and how the destructive messages being despatched can be blocked.







